Examples of Phishing e-mails
More information about phishing and other dangerous e-mails you can found here.
Phishing from a broken university employee account
2025-07-19
If a fraudulent email is really sent from a university employee’s email account (a broken account), it makes it look more trustworthy.
How do you know if it’s a scam?
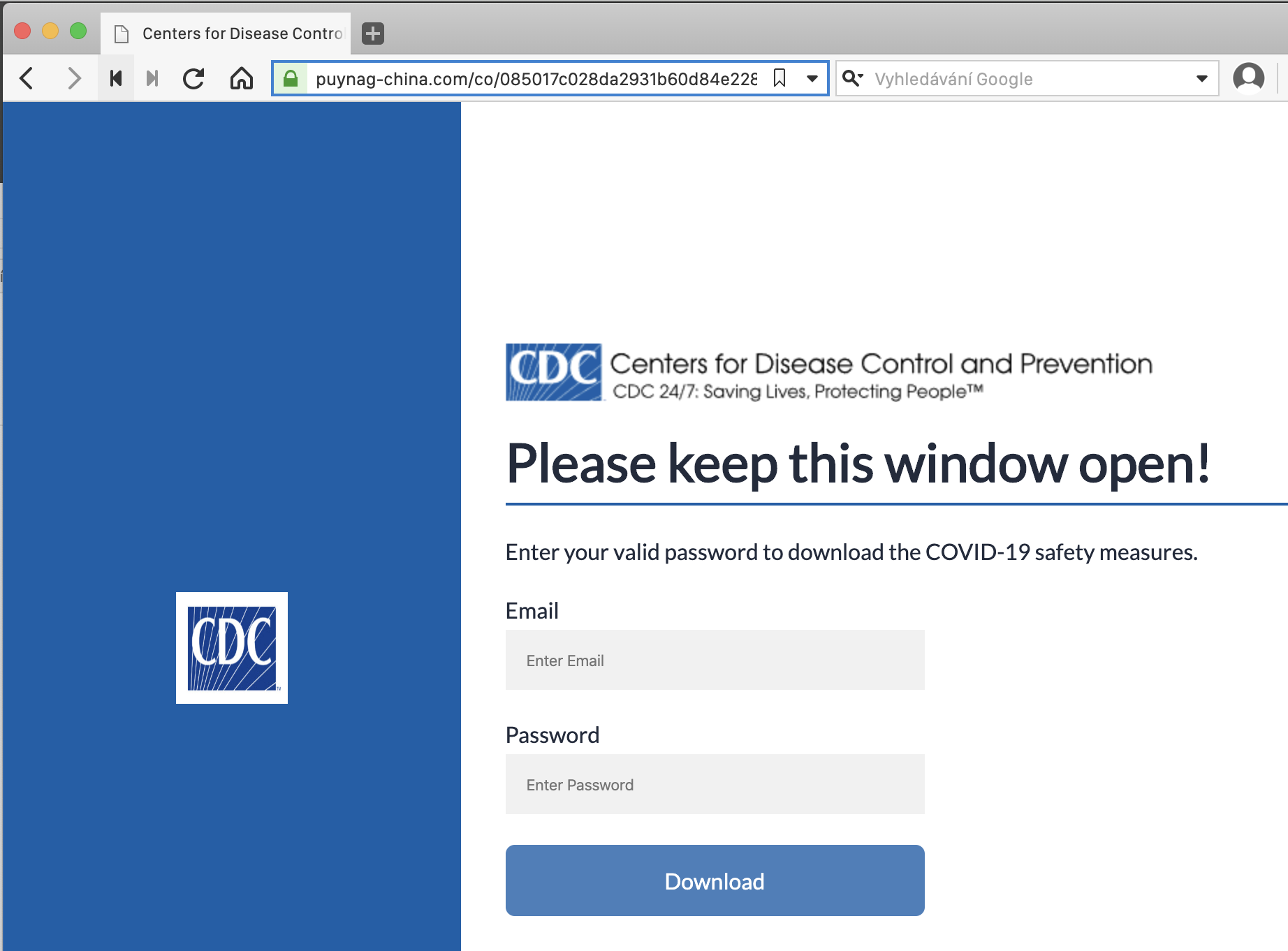
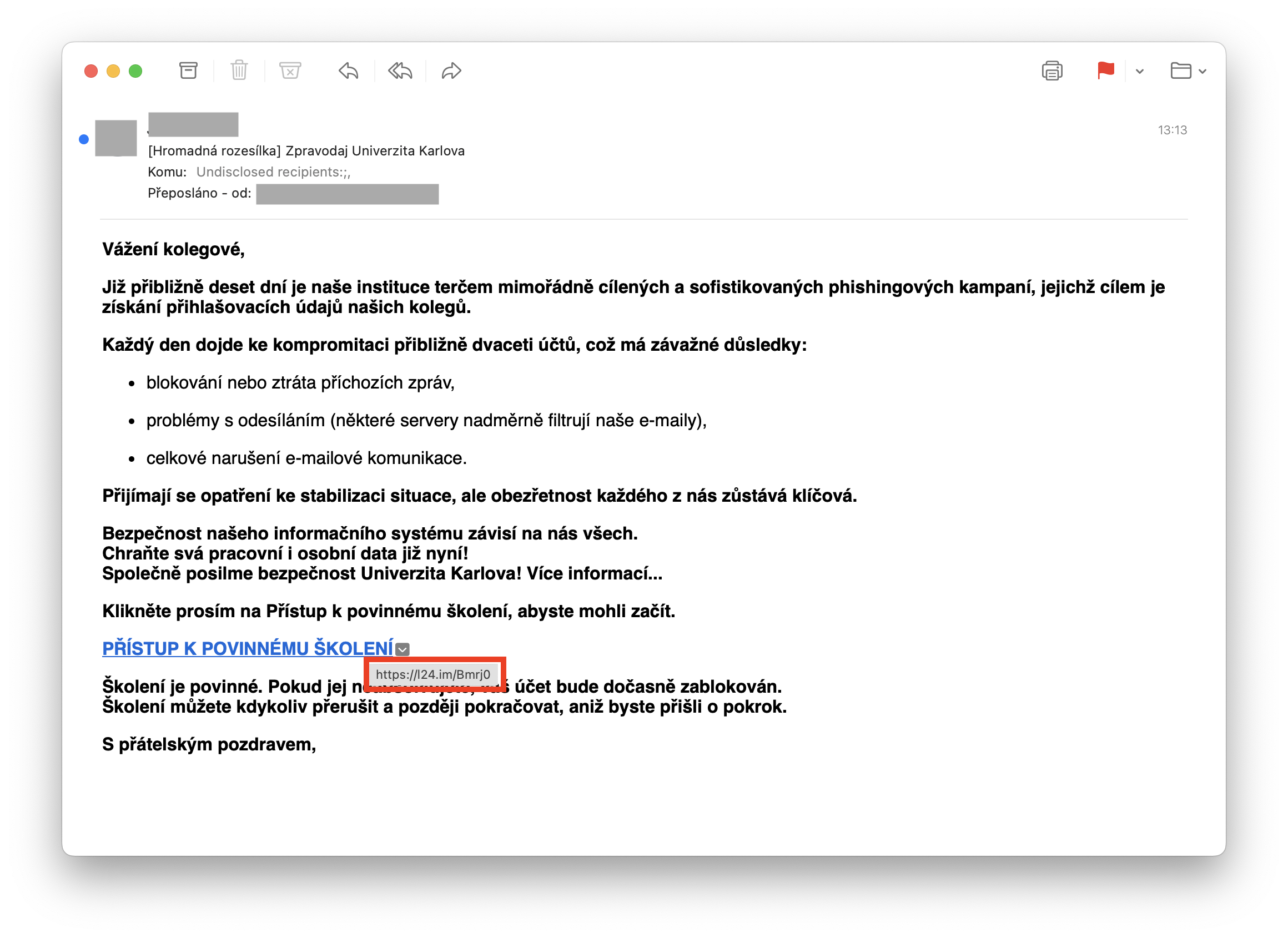
There are more flags, but the main one is that links to a website that isn’t in the university domain! The URL of the site is “https://l24.im/something” .
To find and verify the URL, point the mouse to the link text in the email, wait a while and the link URL will appear (you can see it in the screenshot). Or - when it happens that you click on the link and open the page - you see it in the browser line.
Fake CAPTCHA
2025-03-20
Classic phishing tries to manipulate the user into opening a specific website and fill in your login details (or credit card number, etc.) into the form.
But this trick works a little differently.
After clicking on the link in the email, the login form does not appear directly, but the so-called CAPTCHA. It is about mechanism used on websites to distinguish between human users and automated bots. Appears on the web often - wherever the author of the application wants to prevent, for example, automated guessing passwords.
Captcha usually requires you to perform a task that is relatively simple for humans, but for bots difficult.
So no one will be surprised if after clicking on the link in the mail first appears the www page, which is simple Captcha only:

After clicking, another Captcha will appear, which is a bit annoying, but you still just need to one click with the mouse:
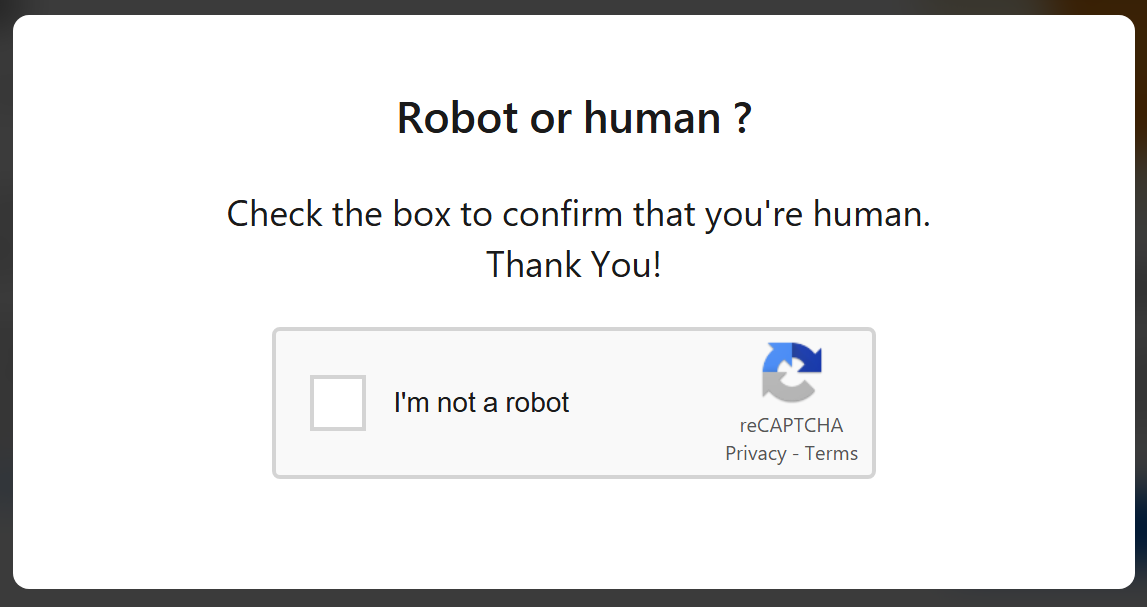
And third, another Captcha, this time a bit more complicated:
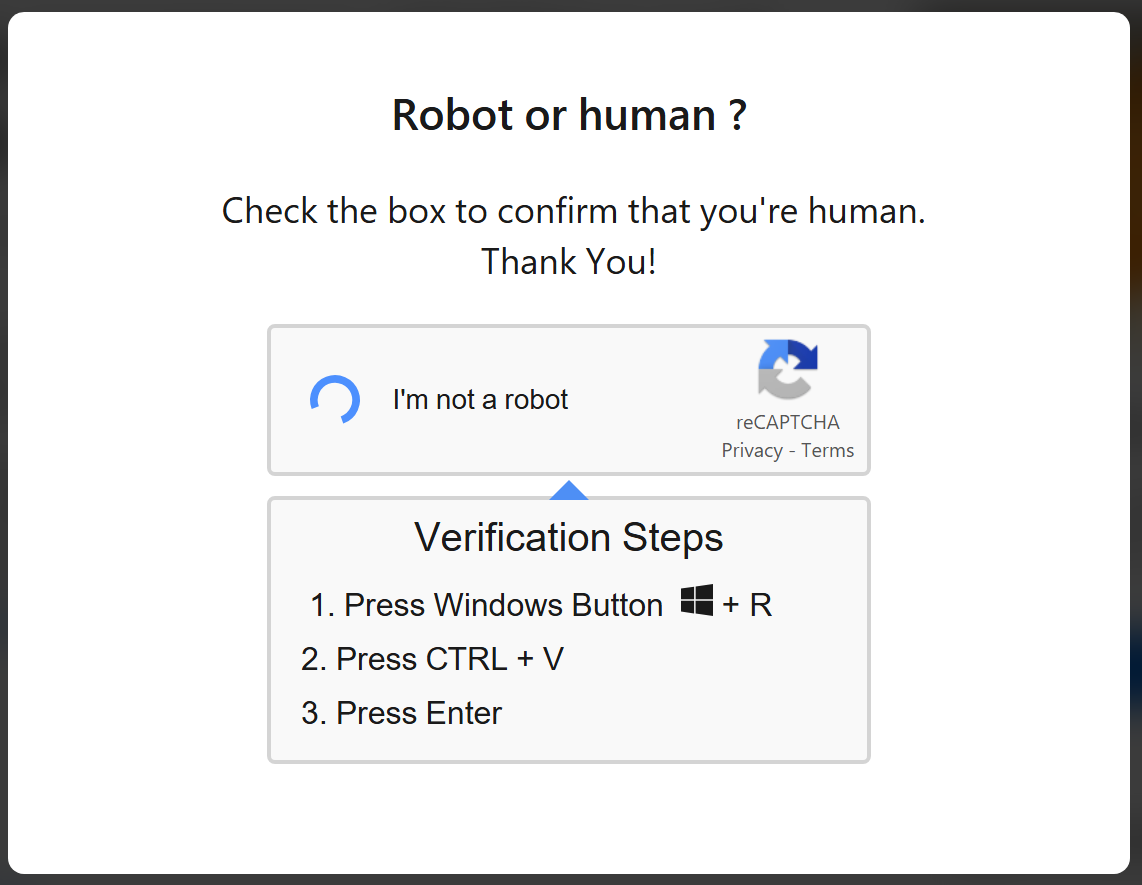
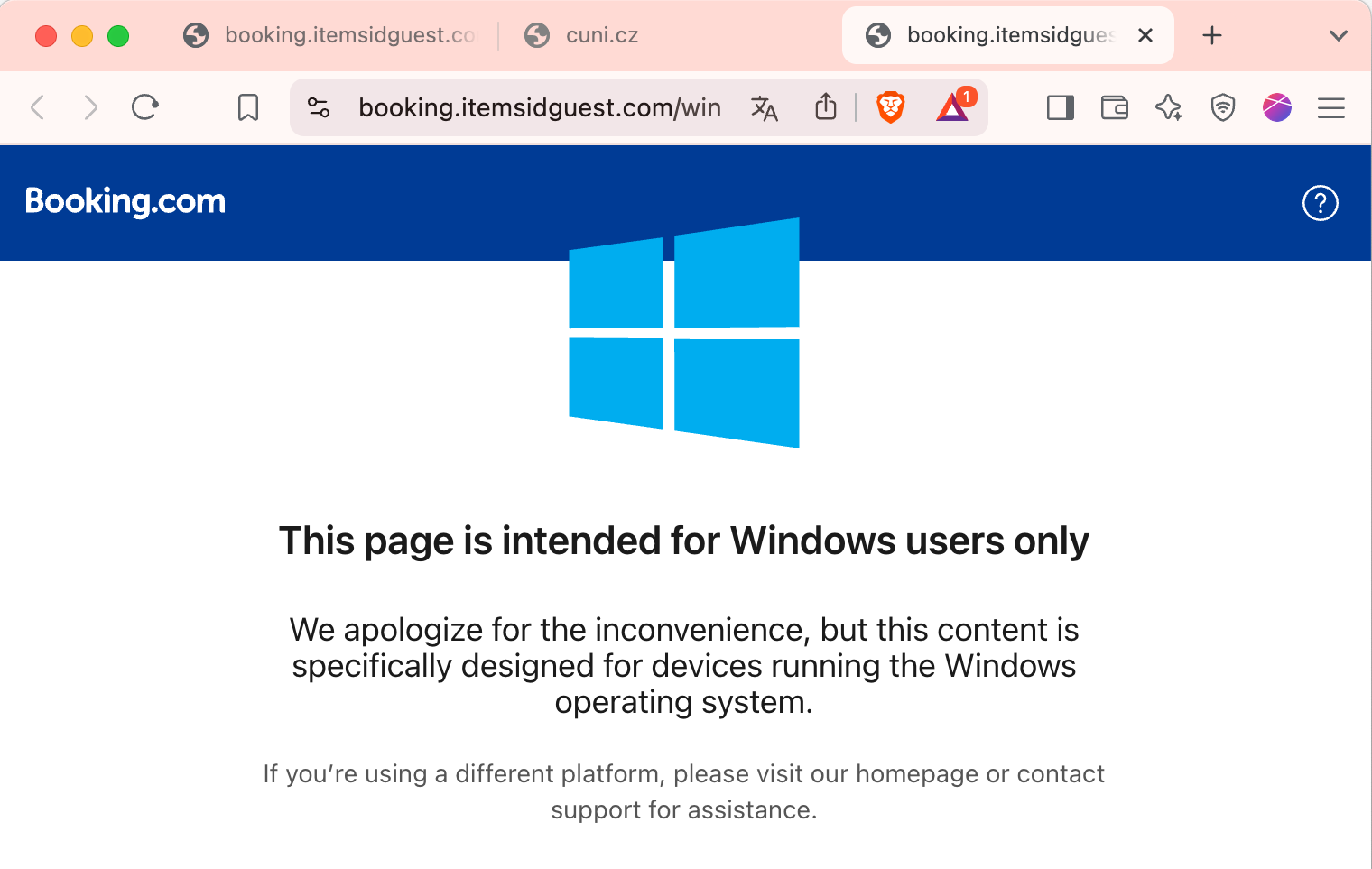
At this point you should be alert. If you will (angry and annoyed by the previous two tests) continue mindlessly, you will virus your computer! The “Windows-R” command will open a window with the command line, the “Ctrl-V” command inserts the contents of the clipboard (where is malware written in PowerShell) and the “Enter” button will start it - and you have a virus-infected computer!
Where did the malware come from in the mailbox? It got there on the previous Captcha test. There was an invisible button in the place of the checkbox and clicking on this button web page insert PowerShell command to system clipboard.
Lesson - do not mindlessly follow instructions during the Captcha test, but wonder if instructions happen not to be something suspicious…
The trick described here works only on Windows. On another operating system (smartphone, Mac, Lin ux…) you will only see a warning that you have an unsuitable operating system.
P.S. if you were distracted but were lucky, your anti-virus program save you
Payment Failed for …
2024-08-30
A common trick is to send a reminder for a payment that failed. In this case, it is alleged to be a failed automatic payment for Apple’s iCloud service.
How do you know if it’s a scam?
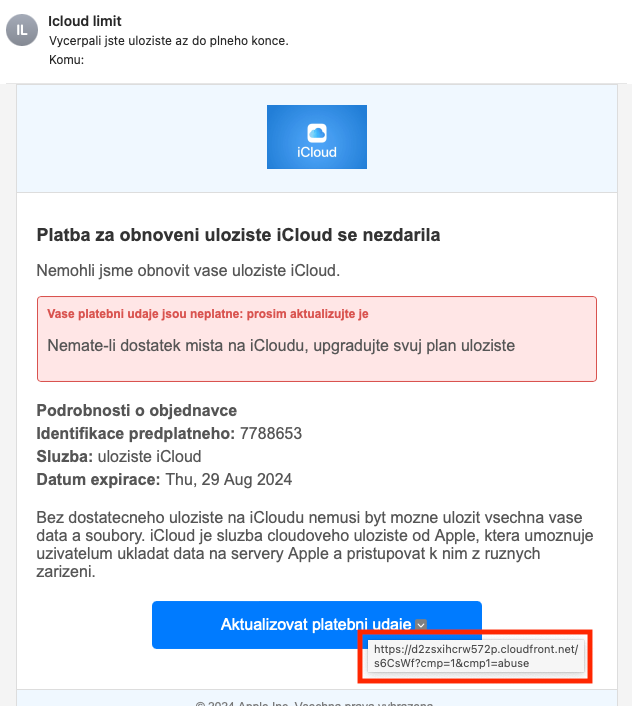
- the sender’s name is “icloud limit” but the sender’s address is not from the apple.com domain
- under the “Update Payment Details” button, there is a link to a domain that has nothing to do with Apple.
To find the real link, move your mouse cursor over the button and wait a while - it will appear. You can still find out the real sender’s address.
Fraudulent mail:
Be careful with QR codes
2023-08-25
Fraudulent phishing that looks like an email from the university’s IT support with information about the introduction of multi-factor authentication and invites you to photograph the QR code with your mobile phone.
This is a trick. When you photograph the QR code with your mobile phone, the fraudulent form is downloaded to your mobile phone and displayed on it. On your mobile phone the anti-virus program is not running and probably isn’t even connected to the Internet via the university network, so the attacker can bypass our protection.
QR codes are commonly used and we see them on electricity bills, on information signs in the park and so on. In this case, however, you should note:
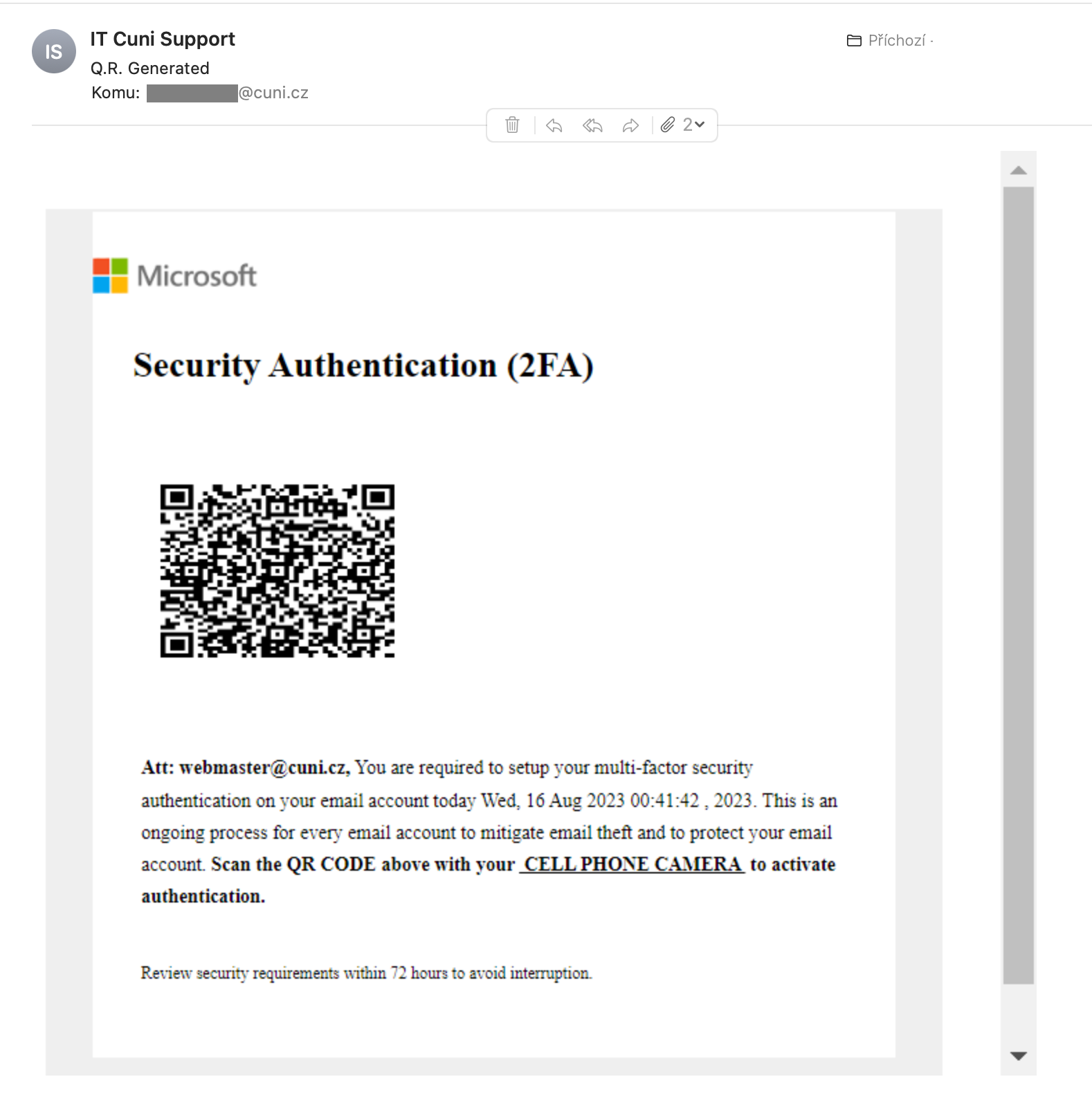
- the sender’s name is “IT Cuni Support” but after clicking on the name, the address from the university domain does not appear cuni.cz, but the address on Gmail.
- the mail has no signature, you don’t know who allegedly sent it, there’s no place to check its authenticity
- the QR code is not square and the whole text is somehow harder to read - that’s because the whole email is one big one image - technique used to make phishing go through a spam filter
- password entry form that appears on the phone after taking a photo of the QR code, does not lead to the university domain cuni.cz
Fraudelent mail:
Fraudulent page with the form:
Document only after login
2022-11-08
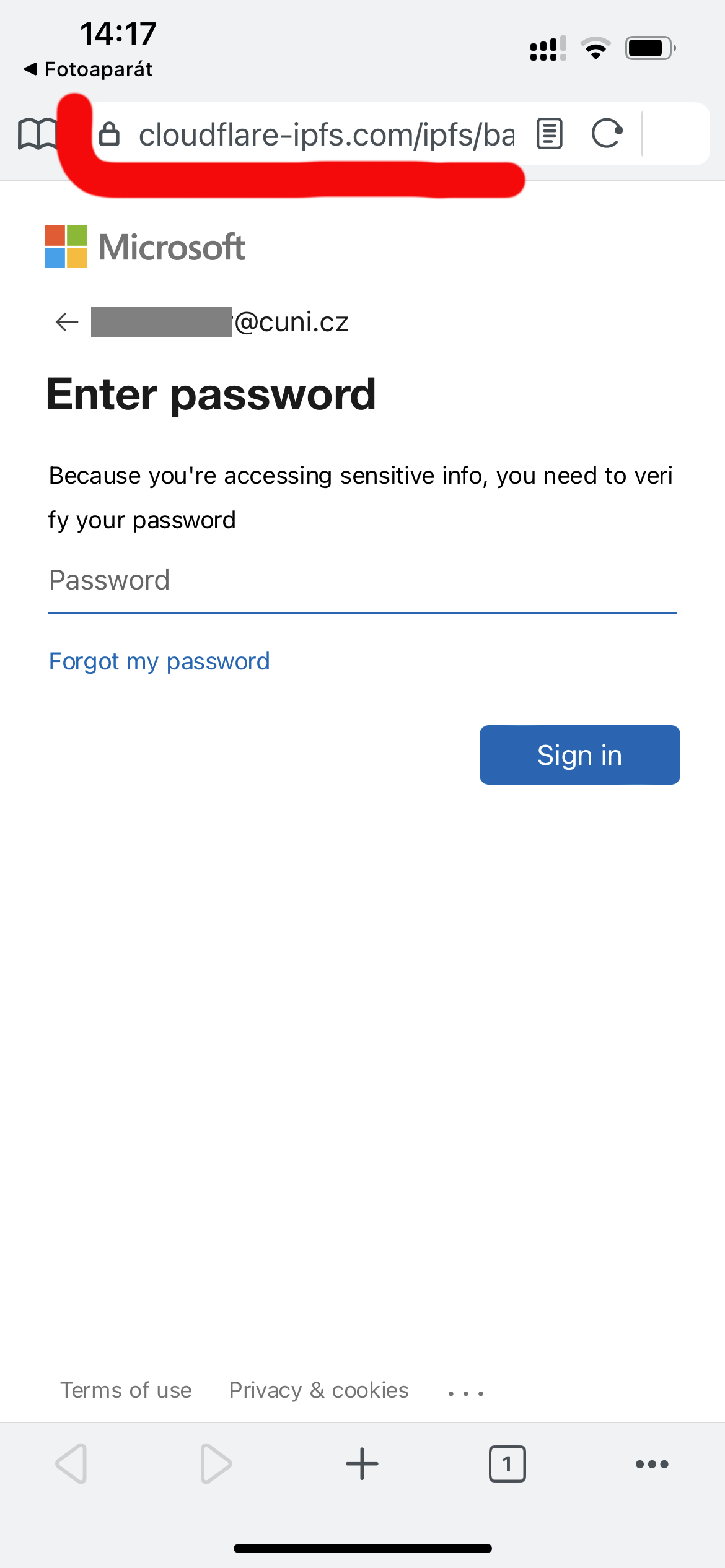
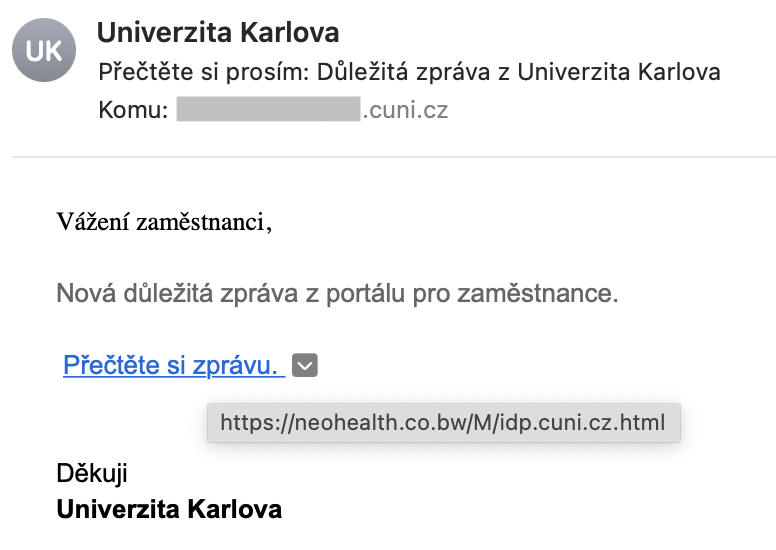
There is nothing wrong with sending an e-mail link to a document in the cloud, which you can only access after login, and we will be seeing more and more of it. But it is also a common trick of fraudsters - so be careful not to fall for phishing! Always check if the page with the login form is trustworthy - especially if the URL of the page is the domain of the organization whose password you should fill in. In this case, the domain of Charles University cuni.cz.
Suspicious:
- the sender of the e-mail is “Univerzita Karlova”, but when clicking on the sender, the address ending at @cvut.cz will appear
- when you move the mouse over the link (text “Read the message”), the link will appear. And it is not Charles University domain name cuni.cz, but to neohealth.co.bw.
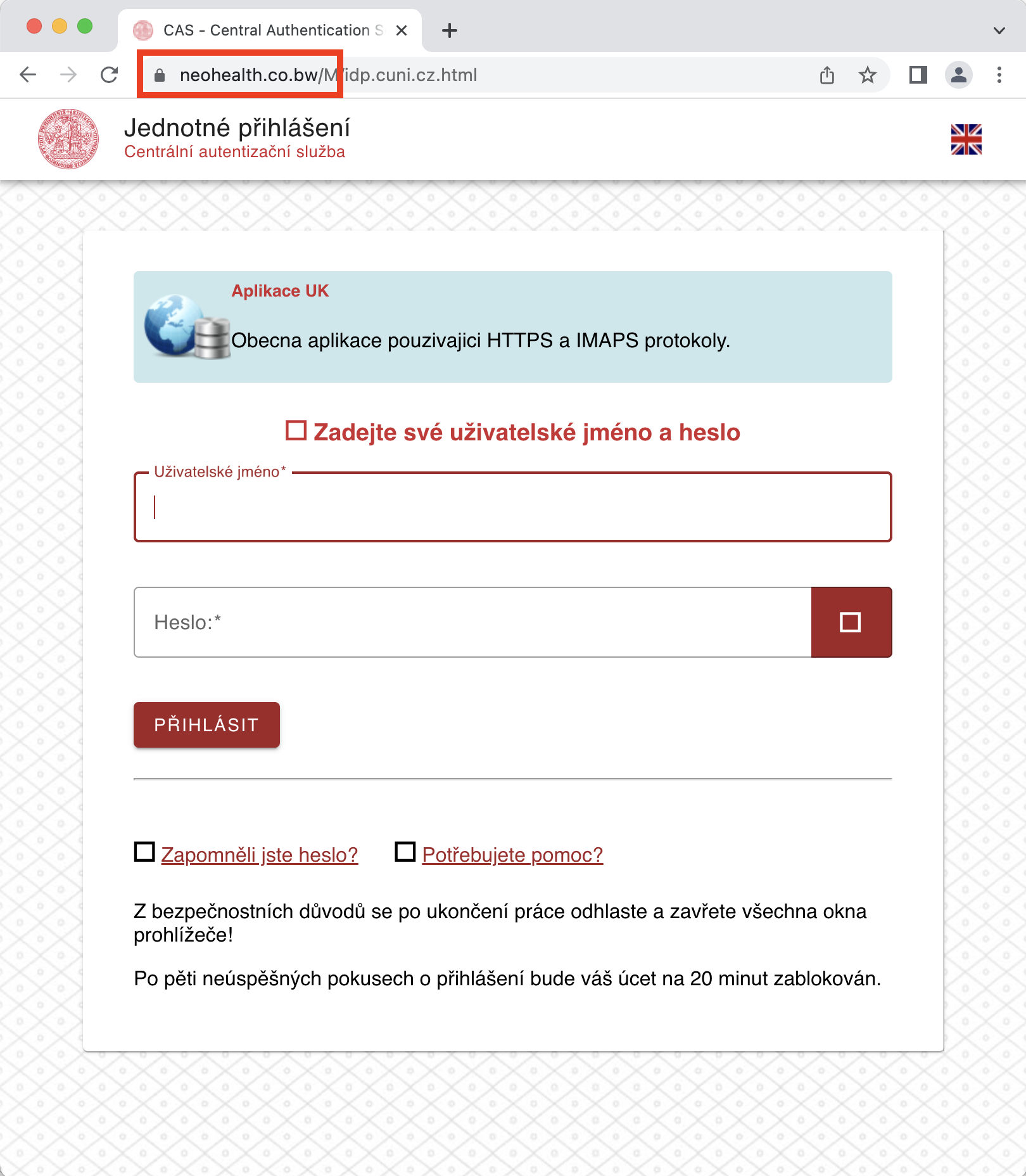
- the website looks exactly like the Central Authentication Service of the UK, but according to the URL the page (top row, marked in red) is not in the university network (in the domain cuni.cz)
Fraudulent mail:
Fraudulent page with the form:
Phishing form with university website background
2022-11-07
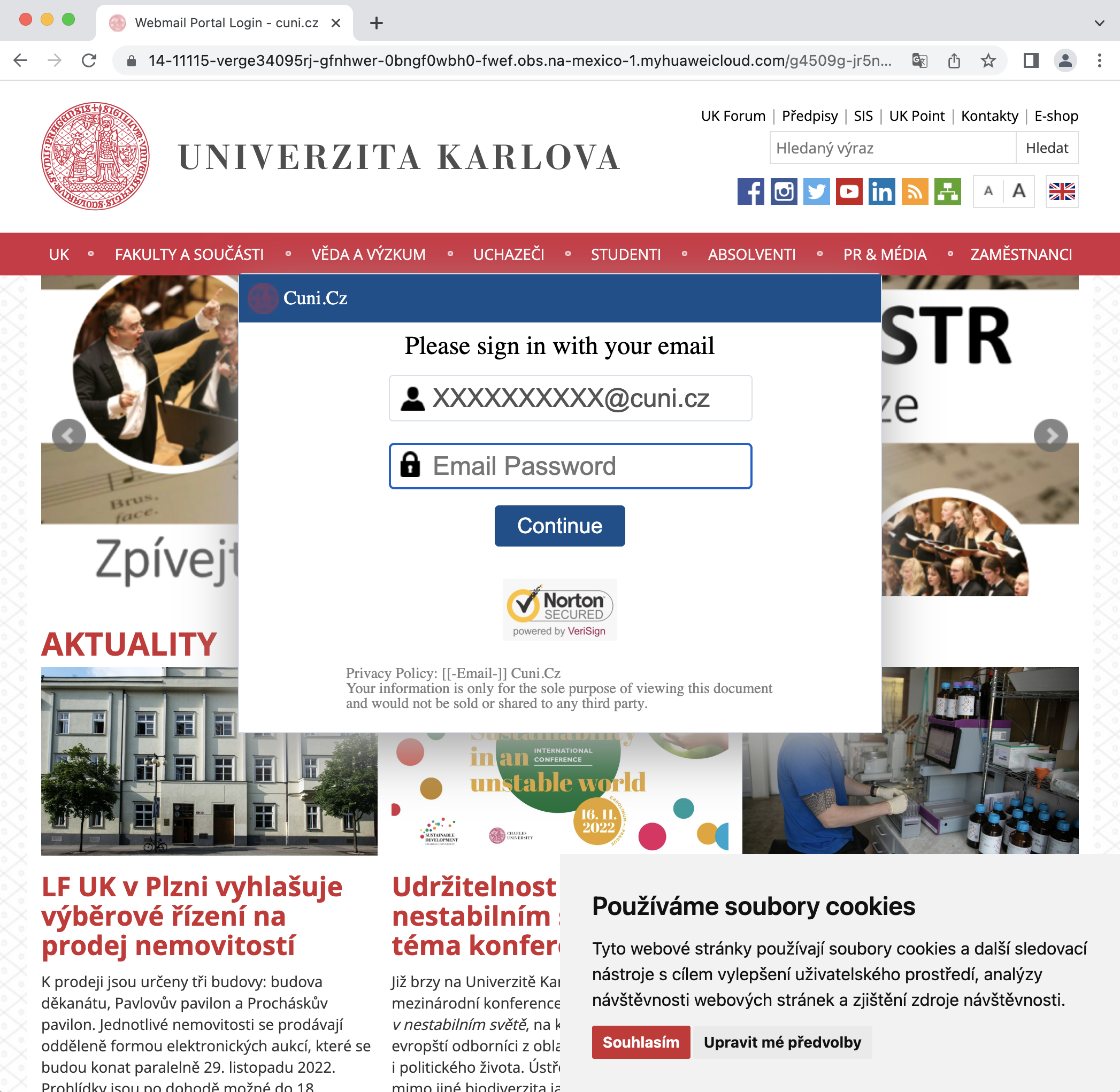
Lately, phishing forms have an up-to-date organization website in the background. They try to give the user the impression that they have reached their home site and just have to log in to get information that is not public.
The phishing form page is actually elsewhere (see the URL of the page in the top row of the browser). Cleverly pulls a domain from her email and automatically downloads the page on that domain and adds it as a background. If you look closely at the URL of the page, you will find your email at the end. You can try to put another organization’s domain in it yourself.
Suspicious:
- Page URL “14-11115-verge…mexico-1.myhuaweicloud.com/…” is definitely not a university
Phishing form scam page:
Phishing from @o365.cuni.cz address
2022-02-07
Fraudulent phishing e-mail, credited with the address of the sender with the domain o365.cuni.cz. Unfortunately, the owner of the account received a similar e-mail, succumbed to it and the attacker is now sending more phishing e-mails within the university from his account.
Suspicious:
- the very requirement to fill in a form for an email upgrade
- breakneck Czech
- the sender, which has nothing to do with the administration of the university’s computer network
E-mail:

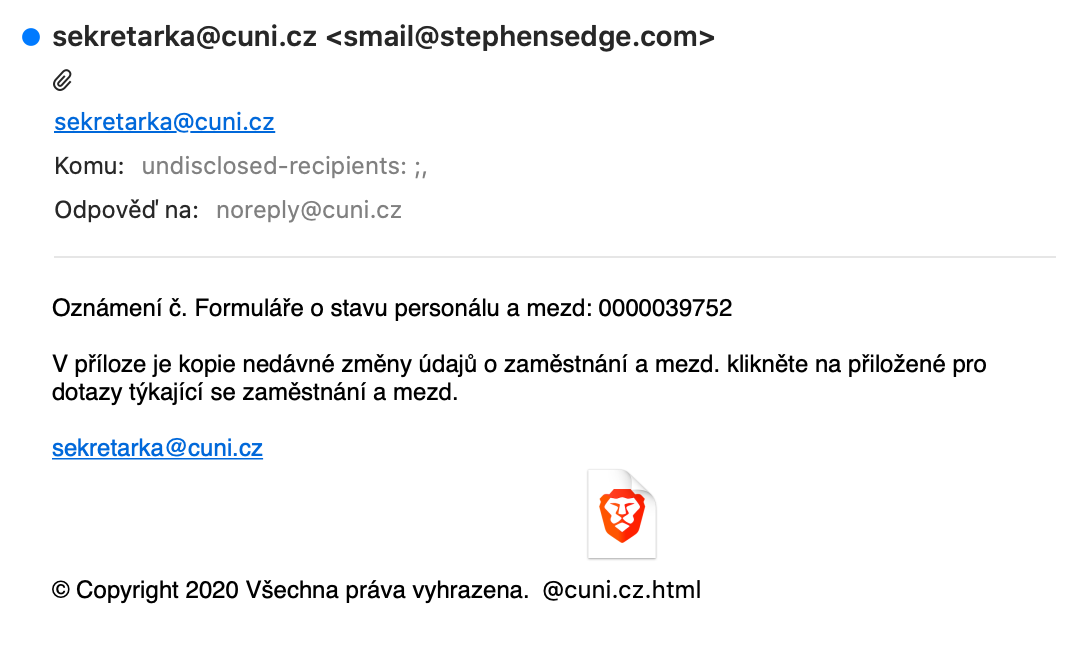
Letter from secretary
2020-10-08
There is no link in this phishing e-mail, but html type attachment with phishing form. And one more bluff – the sender name is “sekretarka@cuni.cz”.
E-mail:
WHO
2020-03-31
It’s exploiting interest in coronavirus information. It looks like an email from the WHO and promises a document with up-to-date information.
E-mail:

Web page with form.
Attention – page is not on WHO domain!